There are no items in your cart
Add More
Add More
| Item Details | Price | ||
|---|---|---|---|
Language: Malayalam
Trainer Support: On WhatsApp
Level: Beginner to Intermediate
Validity Period: 365 days
Includes Concepts + Practical Demo
Scenario based learning
Included best practices for a hands-on understanding
Trainer support for 1 Year on WhatsApp
Hands-on Lab:
NGFW, IPS, Proxy, SSL Inspection, Attack Mitigation using NGFW
Hands-on Lab:
Linux OS/Windows OS Access Controls
File/Directory Permission Management
Analysing Events and Logs
Hands-on LAB:
Traffic inspection
Hash decoding
Hands-on LAB:
Least Privilage Access
Infrastructure Security Design
Open Source SIEM Tool Demo
Vulnerability Assessment
LAB/Activities are planned in such a way that all the learners can do hands-on on their PCs. Trainer will demonstrate or guide learners to setup demo lab.
Minimum PC Hardware Specs: Intel i3 Processor/ AMD, 8 GB RAM, 40 GB HDD.
Software : Linux/Windows OS, Virtual Box/Vmware Player
Licenses: Opensource Appliances/Applications
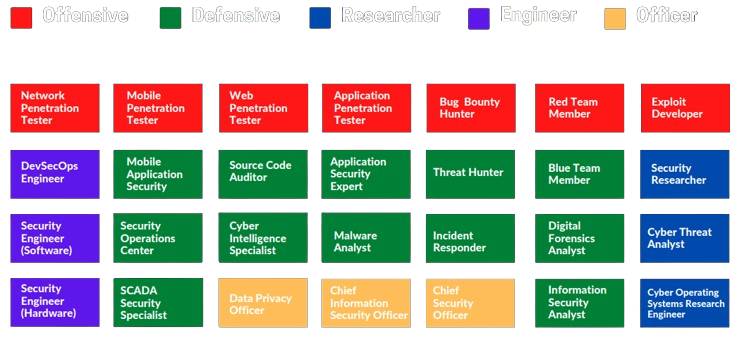
The field of cybersecurity is dedicated to safeguarding digital systems, networks, and data from unauthorized access, attacks, and damage. Cybersecurity professionals play a crucial role in protecting individuals, organizations, and governments from cyber threats, such as malware, ransomware, phishing, and other malicious activities. They employ a range of tools, technologies, and strategies to identify vulnerabilities, implement robust security measures, and respond effectively to incidents.